PureDome Device Posture Check (DPC) allows admins to check and evaluate team member devices according to predefined security rules and ensure that only devices that comply with their predefined security rules can connect to the PureDome network.
Device Posture Check examines the connecting device either during the connection or at regular intervals set by the administrator. By using policies that vary for different teams, it adds an additional layer of security to safeguard sensitive resources effectively.
Create device posture check profiles
- In order to add a Device Posture Check profile, click the Device tab in the PureDome console on the left side.
- Click Posture Check.
- Click Add profile.
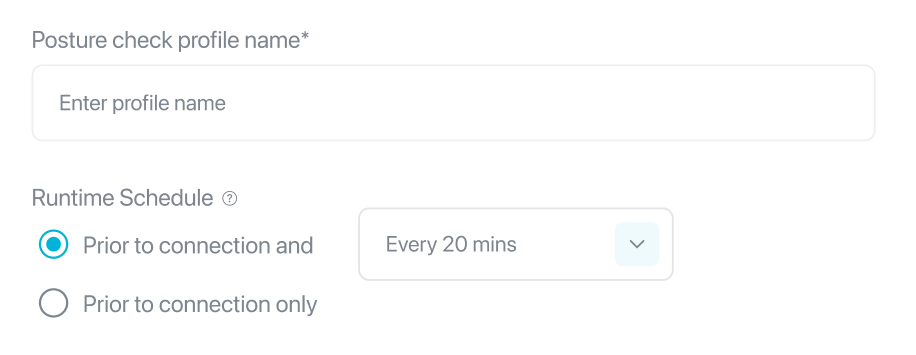
- Enter a Posture check profile name.
- Select the team(s) that should comply with the posture check profile.
Note: The Device Posture Check profiles will be applied to all the team members added to a team.
- Select the suitable Runtime Schedule.
Note: The Device Posture Check profile can be verified either while a team member is connected to PureDome or with every connection to PureDome.
Define posture check specific to each OS
Admins have an option to create different profiles for different operating systems within the same setup or generate separate profiles for each OS.
Each OS profile can have one or more rules which must be met in order to gain access to the PureDome network.
Windows
- Click Add OS to profile.
-
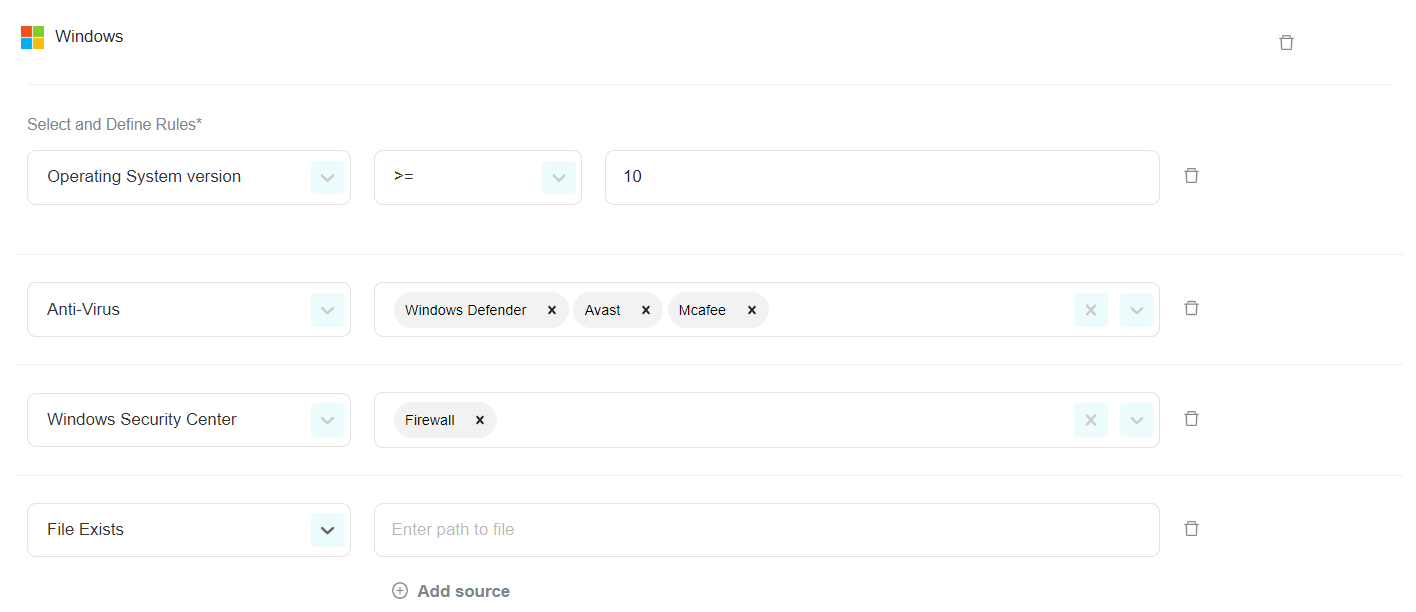
Select and define rules.
You can pick from the following options:
Antivirus: PureDome will verify whether the device has the organization’s preferred antivirus software installed.
File-Exists: PureDome will verify the presence of a specific file in a specific path.
Disk Encryption: PureDome will verify whether the OS hard-drive is encrypted.
Certificate: PureDome will verify the presence of a specific certification on the device. (in the local Windows CA store)
Process Running: PureDome will verify whether a specific process is currently running on the device.
Registry: PureDome will verify the existence of a specific registry path or value in the device’s Windows Registry.
Operating System version: PureDome will verify that the device is using an excepted OS version (equal to and/ or higher than).
Active Directory association: PureDome will verify the user's "login_domain" matches what is specified in the rule.
Windows Security Center: PureDome will verify the status of the selected Firewall, or Antivirus is showing as "Good".
Block Torrenting: PureDome will block all peer-to-peer (P2P) traffic on the end user's device.
Device Inactivity: If there is no activity on the user's device for 15 minutes, the PureDome application will automatically log out.
- Click Add rule to OS (if needed)
macOS
- Click Add OS to profile.
-
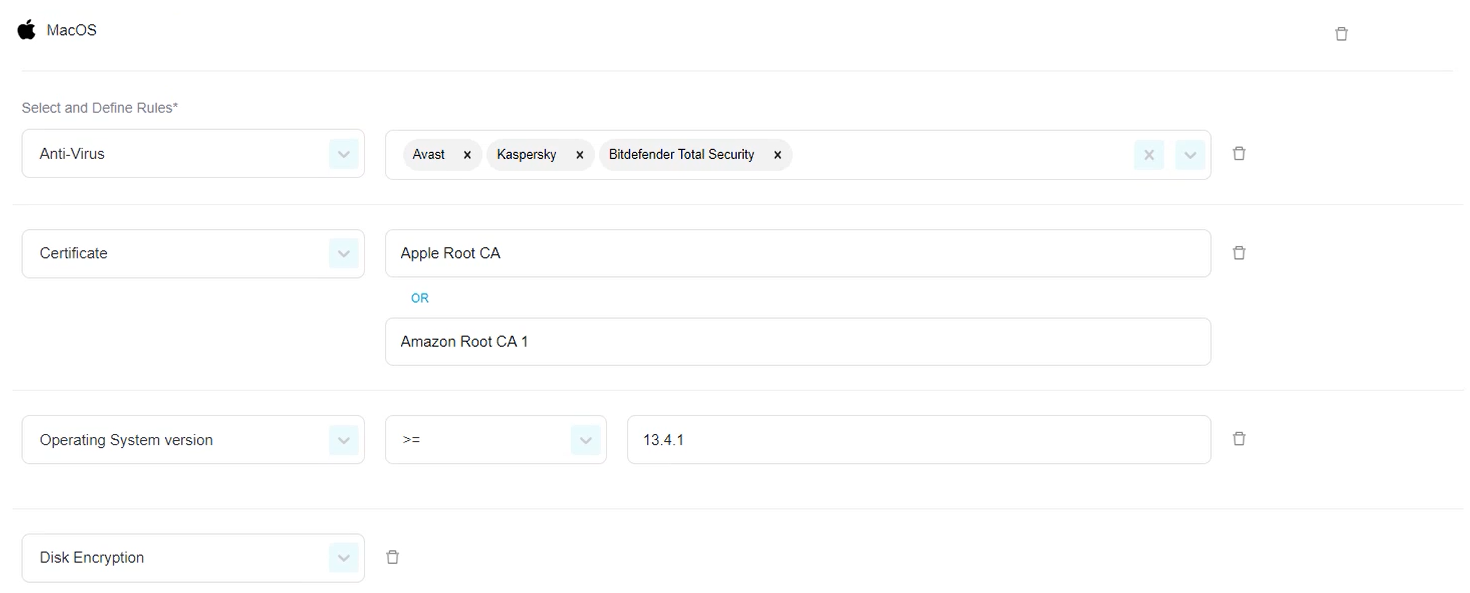
Select and define rules.
You can pick from the following options:
Antivirus: PureDome will verify whether the device has the organization’s preferred antivirus software installed
File-Exists: PureDome will verify the presence of a specific file in a specific path.
Disk Encryption: PureDome will verify whether the OS hard-drive is encrypted.
Process Running: PureDome will verify whether a specific process is currently running on the device.
Certificate: PureDome will verify the presence of a specific certification on the device. (macOS Keychain).
Operating System version: PureDome will verify that the device is using an excepted OS version (equal to and/ or higher than).
Block Torrenting: PureDome will block all peer-to-peer (P2P) traffic on the end user's device.
- Click Add rule to OS (if needed)
Linux
- Click Add OS to profile button.
-
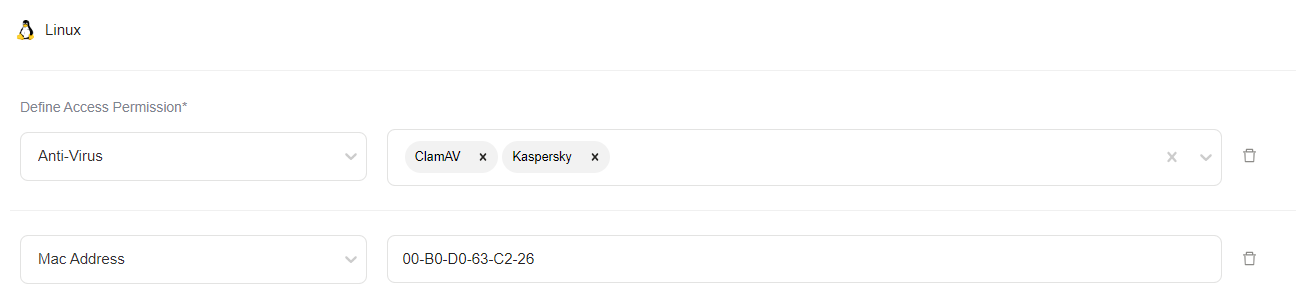
Select and define rules.
You can pick from the following options:
Antivirus: PureDome will verify whether the device has the organization's preferred antivirus software installed.
Process Running: PureDome will verify whether a specific process is currently running on the device.
File-Exists: PureDome will verify the presence of a specific file in a specific path.
Mac Address: PureDome will verify the presence of the specified MAC address on the network.
Block Torrenting: PureDome will block all peer-to-peer (P2P) traffic on the end user's device.
- Click Add rule to OS button (if needed)
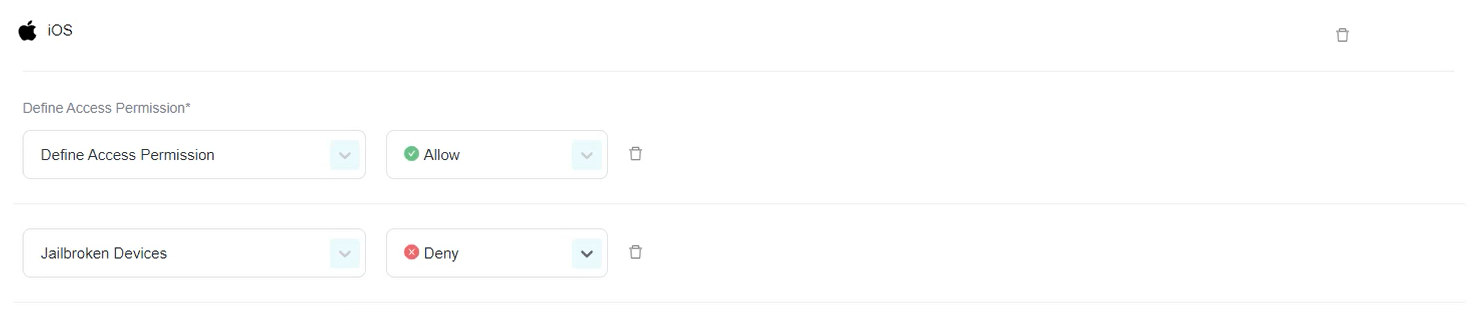
iOS
- Click Add OS to profile.
-
Select and define rules.
You can pick from the following options:
Allow: Mobile devices using the PureDome application will be allowed into the PureDome network.
Deny: Mobile devices using the PureDome application will be denied access into the PureDome network.
Jailbroken Devices: Jailbroken devices will either be allowed or denied access into the PureDome network.
- Click Add rule to OS (if needed)
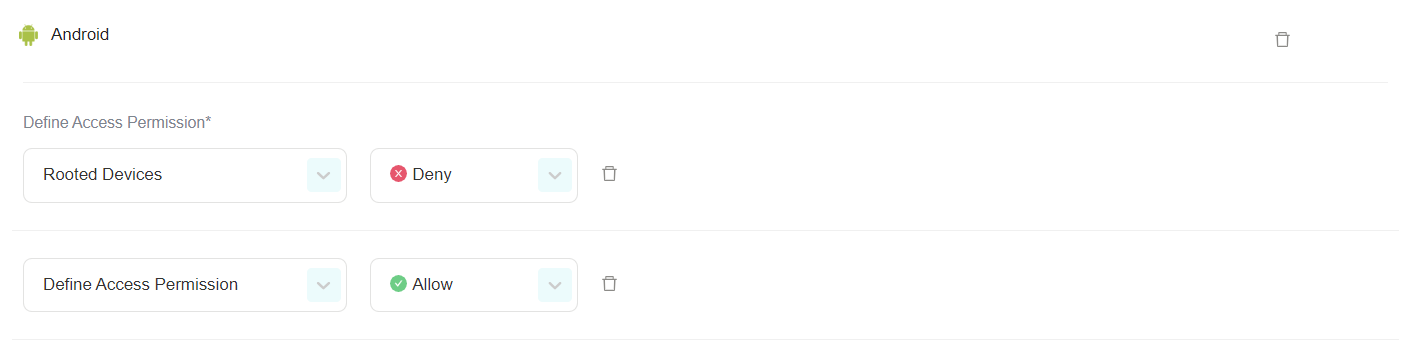
Android
- Click Add OS to profile.
-
Select and define rules.
You can pick from the following options:
Allow: Mobile devices using the PureDome application will be allowed into the PureDome network.
Deny: Mobile devices using the PureDome application will be denied access into the PureDome network.
Rooted Devices: Rooted devices will either be allowed or denied access into the PureDome network.
- Click Add rule to OS (if needed)
Note:
Supported app versions for DPC:
Windows: v2.1.5.3 and above
macOS: v2.1.0 and above
Linux: v1.2.0 and above
iOS: v2.1.0 and above
Android: v2.2.44 and above
Set contextual access & session timeout
Set contextual access & session timeout is a part of the Zero Trust Network Access (ZTNA) principle. This feature provides enhanced security by allowing account administrators to define precise conditions for user sessions. This feature ensures that users are logged out of the system based on specific states, regardless of their activity or connection status.
Here’s how you can enable session timeout as an administrator:
- Click the Devices tab in the PureDome console on the left side.
- Click Posture Check.
- Click Add profile.
- Enter a Posture check profile name.
- Select the team(s) that should comply with the posture check profile.
- Select the suitable Runtime Schedule.
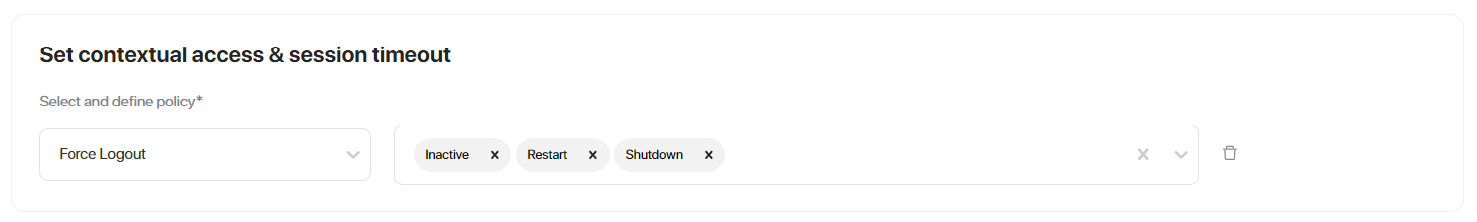
- Scroll down to the Set Contextual Access & Session Timeout tab.
- Click Add contextual rule.
- Select and define policy.
- Click Apply.
Setting a session timeout limit enhances security by ensuring sessions do not remain open indefinitely. This is particularly crucial in environments where sensitive information is accessed.
Note:
Supported app versions for session timeout:
Windows: v2.2.5.9 and above
Proxy and Manual Connections
Here’s how you can block gateway connections on proxy extensions:
- Click the Devices tab in the PureDome console on the left side.
- Click Posture Check.
- Click Add profile.
- Enter a Posture check profile name.
- Select the team(s) that should comply with the posture check profile.
- Select the suitable Runtime Schedule.
- Scroll down to the Proxy and Manual Connections tab.
- Check the box to enable the option to block Gateways on Proxy Extension.
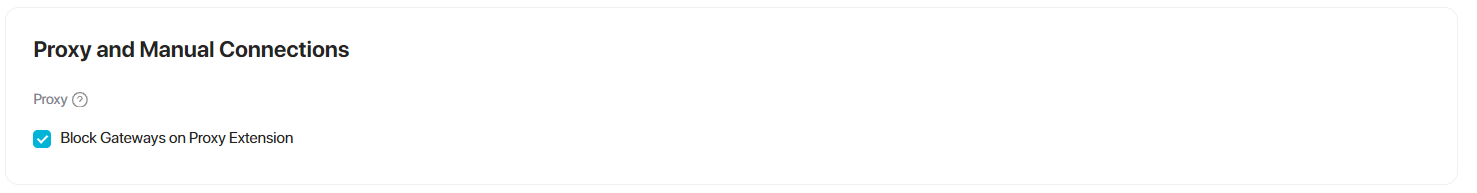
Enabling this option will block gateway connections on PureDome browser extensions.
If you have any questions or are experiencing any issues, please don't hesitate to contact our 24/7 customer support team via live chat or email at support@puredome.com. We're always happy to help!